How to avoid being a victim of phishing?
Have you ever been looking at photos on Instagram and suddenly you get an email saying that someone has tried to log into your bank account and you should click on the following link to check it out? If so, you may be yet another victim of phishing.
Today, we live in a highly digitalised world and fraud is a daily occurrence. Phishing is one of the most common and consists of the theft of confidential information by means of identity theft to carry out further crimes. Do you know how to defend yourself against this threat? Don’t worry, we’ll show you how. Join us!
The most important thing to know
Phishing is a fraudulent practice that has gained prominence in recent years due to the profits generated by using it. Attackers often carry out this crime through social networks, online games and job offers. They collect information using malicious software, pharming, DNS and content entry, among other methods.
Special attention should be paid to emails that have URLs with special characters or do not have the letter ‘s’ at the end, and avoid opening emails from unknown senders and links to them as much as possible.
This can be done not only through e-mails but also through other modalities including phone calls or text messages. In all of them, the messages ask for your immediate attention, as they seek to confuse the victim.

What is phishing?
It is a form of social engineering designed to convince a victim to hand over personal information. It is done electronically and in return, a profit is received. It has a huge financial impact on the companies or individuals who suffer from it.
What is to be gained from this practice?
The term comes from the English “fishing” and refers to fishing by means of “hooks” (traps) to obtain valuable information. It has become more important thanks to the rise of the internet and brings some benefits to those who engage in it. It is one of the most common computer frauds. Some of its main objectives are the following:
- Financial gain: Obtaining money by means of stolen banking credentials.
- New identity: There is also the sale of identities to criminals to camouflage their activities.
- Fame: Victims are targeted for peer recognition.
How are phishing attacks classified?
Most attacks are carried out through fake e-mails that lead the victim to fake websites via a URL. They can be classified as follows:
Attacks usually occur via e-mails. Cybercriminals impersonate reputable organisations that need personal information from the victim. Generally, the messages sent cause an emotional impact, either by instilling fear or by making them believe that they have won a prize. Victims then enter their details into a fraudulent link.
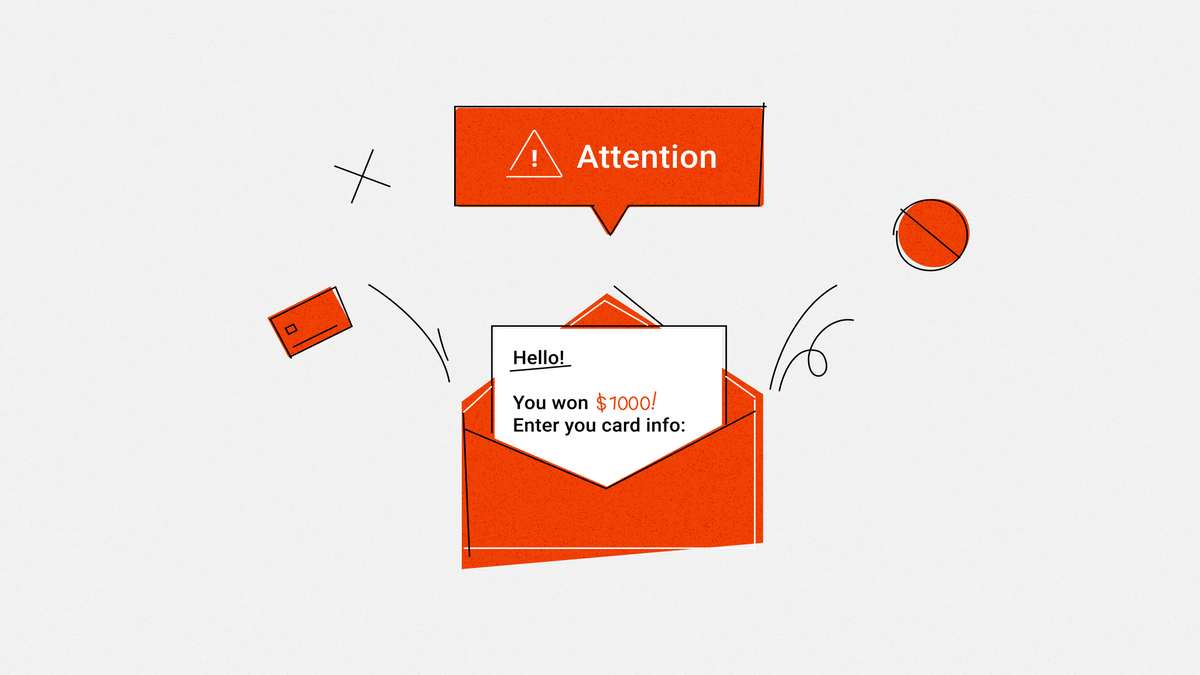
How to recognise phishing?
In general, text messages or e-mails are intended to confuse the victim emotionally so that he or she will open them as soon as he or she sees them. Some phrases used or methods may include the following :
- There is some suspicious activity or login attempts on your accounts.
- You want to verify some personal information.
- Coupons for free products or discounts.
- You have won cash prizes or vehicles.
- You have been eligible for a government rebate.
- If the URL of the page contains CE (foreign character).
- If the URL has special characters such as @.
What is phone phishing?
This method is also called vishing. It consists of phone calls where the scammers pretend to be banks, the police or even government organisations. They tell the victim about a problem with their accounts that must be solved immediately. To do so, they ask for the victim’s details or inform them that they need to cancel a fine.
Usually, cybercriminals or hackers ask the victim to pay via bank transfers or credit cards, as they are more difficult to trace. Related to this method is smishing, which refers to text messages in the same way.
What are the stages of phishing?
Knowing the different phases of phishing helps us to prevent this crime. Many studies have identified 6 phases:
Planning: Here the attacker chooses his victim, the method, the organisation he intends to impersonate, the means to be used and what he wants to achieve: passwords, card numbers, among others.
Preparation phase: There are differences in the way the attack is carried out because depending on the type of information to be obtained, the means will be different. The following are some scenarios:
- Personal mailings: The work must be more complex because the information is personalised.
- Mass mailings: When dealing with collective recipients such as prize winners, less elaboration is required.
- Organisational or corporate mailings: This is more complex because it requires knowledge of how the organisation or company works to avoid arousing suspicion. In many cases, the fraudulent pages carry the same logo.
- Attack: It has to do with calls, sending emails or text messages. Most commonly, the victim is asked to fill in a questionnaire via a fake link.
- Data collection: If the victim is required to enter data, then wait until he/she does so. If a virus is being uploaded to the server, then the programme must be run to get the information.
- Execution of the fraud: Once the desired information is obtained, it is used for the benefit of the attacker himself or he may sell the data to others for further crimes.
Social engineering is the act of fraudulently obtaining information from people through psychological techniques and social skills. Its purpose is to use this information against themselves or their organisations.

Tips on how to avoid phishing
This crime is becoming more and more frequent. Therefore, some recommendations should be taken into account:
- Do not open e-mails from unknown persons. You can mark them as spam.
- Avoid falling for threats. Remember that banks do not ask for personal information, as they already have it in their databases.
- If you are asked to enter confidential data, check that the URL begins with “HTTPS” instead of “HTTP”, as the “s” stands for secure.
- Read domains carefully. Fake domains usually have misspellings.
- Do not open files or click on links in suspicious emails.
Summary
Phishing is an increasingly common practice because of the ease with which organisations, individuals or companies can be impersonated. The most common means of phishing is through emails. However, it is also carried out via text messages or phone calls.
The best way to prevent it is to carefully read the content of everything sent. Before taking any immediate action, stop and check with search engines. If the page that has communicated with you usually does so, or if it exists in principle, check its URL and do not open attachments for any reason.
If you found our recommendations useful, leave us a comment and share this article on your social networks.